Protect Your Online Investments: An In-Depth Manual on Managing User Access with Cloudflare
In an age where cyber threats loom large, maintaining control and security over your online presence is non-negotiable. However, the need for collaboration and delegation of tasks is equally vital in the fast-paced world of Web Design management.
In this comprehensive guide, we’ll walk through how you can leverage Cloudflare’s user access feature to delegate tasks securely, fostering efficient teamwork while safeguarding your most critical digital assets.
Giving someone access to Cloudflare can be as simple as sharing the login credentials, but what if you don’t want to give them full control? Fear not, there is a way to grant user access without sacrificing your security.
With Cloudflare’s flexible permissions system, you can give others access to specific sections of your account without granting them full control. It’s easy to set up and can save you a lot of headaches in the long run. So why not give it a try?
Below is a step by step guide on how to Grant a User Access to your Cloudflare
Step 1
Go to www.cloudflare.com
Step 2
Click on Log In

Step 3
Click on your domain

Step 4
Click on Manage Account

Step 5
Click on Members

Step 6
Click on Invite

Step 7
Type the individuals name that you want to give access to.
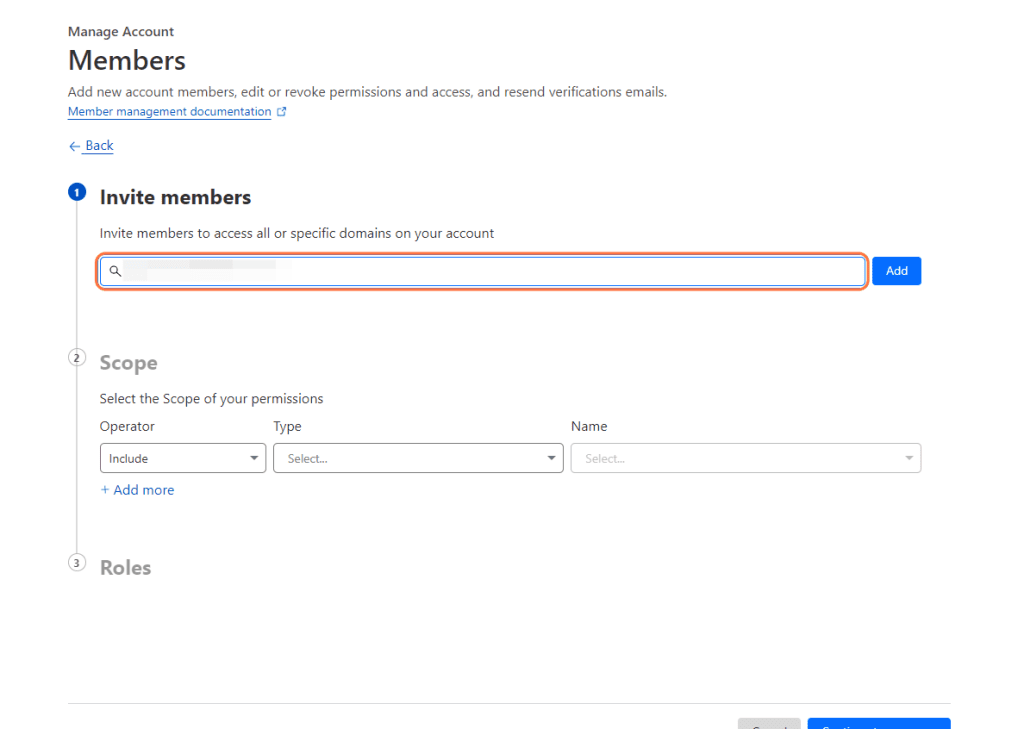

Awesome, you’re all set! Just hit that save button and you’re golden. That user’s email address will officially be granted entry into your Cloudflare account.
Enjoy the access!
Understanding Cloudflare User Access
Allowing multiple users to manage a single web property without compromising security might sound like walking a tightrope, but Cloudflare’s method is akin to securely fastening a harness before stepping out onto the wire. By dividing user roles and permissions into fine-grained controls, Cloudflare ensures each user operates within a well-defined boundary.
Roles and Permissions: The Lingo of User Access
Cloudflare bestows four primary roles on its users, each with varying degrees of control and access. These are:
- Administrator: The master of the domain, Administrators hold the key to the kingdom. They can modify every aspect of an account and give/take away control from other users.
- User: Users have limited rights, perfect for those who need to monitor or configure certain settings without full account control.
- Billing: As the name suggests, this user can manage the financial aspects of your account, from invoices to payment methods.
- Support: Support users have restricted rights, intended for those who may need to communicate with Cloudflare support on your behalf.
Understanding and correctly assigning these roles will be the first step to structuring your cloud security architecture.
Benefits and Best Practices
The benefits of Cloudflare’s user access system extend beyond security; they also offer unparalleled flexibility in workflow. Here are a few best practices that can help you maximize the potential of Cloudflare’s user access:
- Segregation of Duties: Assigning different roles to different individuals ensures checks and balances, preventing a sole user from making catastrophic changes.
- Regular Audits: Just as seasons change, so do team members and their roles. Regularly audit and update who has access to what to maintain security hygiene.
- Password Management: Encourage strong passwords, and consider adopting a password manager to reduce the likelihood of a breach due to weak credentials.
Implementing User Access in Cloudflare
User access in Cloudflare is a tool you can sharpen for precision. Here’s how you can set it up:
Adding Users to Your Cloudflare Account
To begin, sign in to your Cloudflare account and head to ‘My Profile’, then ‘Members’. Here, you can invite new users by specifying their email address and role.
Customizing Roles and Permissions
Customization is where the power lies. You can tailor the permissions of each role to fit your organization’s workflow. Perhaps some users need to manage DNS settings, while others should be restricted to viewing analytics.
Using Principals of Least Privilege
The notion of ‘least privilege’ should guide your customizations. Allow only the minimum level of access necessary for each user to perform their required function.
Secure Access: Safeguarding Your Cloudflare Account
Security is not just about the features you use; it’s also about the habits you enforce. Here’s how you can bolster the safety of your Cloudflare account:
Enforcing 2FA
Two-factor authentication (2FA) is a must. Require all users to enable 2FA to add an extra layer of defense against unauthorized account access.
Regular Training and Cybersecurity Updates
Educate your team about security best practices, such as the dangers of phishing and password hygiene. Regular updates ensure everyone is knowledgeable about the latest threats and protections.
Keep on Top of Cloudflare’s Security Features
Cloudflare is actively evolving, which means new security measures are always on the horizon. Stay informed about the changes and see how they fit into your security strategy.
Common Challenges and How to Overcome Them
While Cloudflare’s user access system is robust, you might encounter some hiccups along the way. Here are common challenges and how to tackle them:
Managing Access for Contractors and Third Parties
External collaborators add another layer of access management complexity. Deploy temporary roles or permissions for contractors and revoke them once the job is done.
Balancing Access and Bureaucracy
Rigorous security should not come at the cost of stifling efficiency. Work with your team to strike the right balance between access controls and smooth workflow.
Account Recovery and Data Loss Prevention
Be vigilant about account recovery emails. Always double-check the legitimacy of these communications to prevent data loss or breaches under the guise of recovery processes.
Integrating Cloudflare User Access in Your Organization
For Cloudflare’s user access to be truly effective, it must become a seam in the fabric of your organization’s cybersecurity culture. Integration includes:
Developing Cross-Functional User Access Policies
Collaborate with IT, HR, and any other relevant departments to craft policies that reflect the dynamics of your organization.
Training and Support
Ensure proper training and support are in place for users to understand and use the Cloudflare system effectively.
Continuous Improvement
Regularly review feedback on Social Media and experiences to refine your user access model. Adapt as the needs and structure of your organization evolve.
The Power of Prudent Delegation
With the right approach, user access in Cloudflare is a potent tool that combines functionality with robust security, giving you the power to delegate without fear. By proactively embracing and customizing user roles, employing best practices, and staying vigilant about account security, you can safely share the load without sharing the risk.
Secure your web assets, retain control, and foster a collaborative environment that thrives on trust and efficiency. Welcome to the future of web management—user access done right, with Cloudflare.




